Printer Steganography on:
[Wikipedia]
[Google]
[Amazon]
 A Machine Identification Code (MIC), also known as printer steganography, yellow dots, tracking dots or secret dots, is a
A Machine Identification Code (MIC), also known as printer steganography, yellow dots, tracking dots or secret dots, is a
 In 2005, the civil rights group Electronic Frontier Foundation (EFF) encouraged the public to send in sample printouts and subsequently decoded the pattern. The pattern has been demonstrated on a wide range of printers from different manufacturers and models. The EFF stated in 2015 that the documents that they previously received through the FOIA suggested that all major manufacturers of color laser printers entered a secret agreement with governments to ensure that the output of those printers is forensically traceable.
In 2007, the European Parliament was asked about the question of invasion of privacy.
In 2005, the civil rights group Electronic Frontier Foundation (EFF) encouraged the public to send in sample printouts and subsequently decoded the pattern. The pattern has been demonstrated on a wide range of printers from different manufacturers and models. The EFF stated in 2015 that the documents that they previously received through the FOIA suggested that all major manufacturers of color laser printers entered a secret agreement with governments to ensure that the output of those printers is forensically traceable.
In 2007, the European Parliament was asked about the question of invasion of privacy.
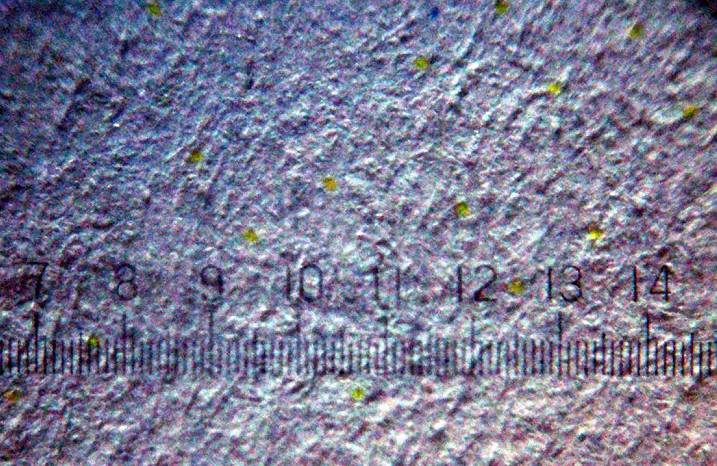
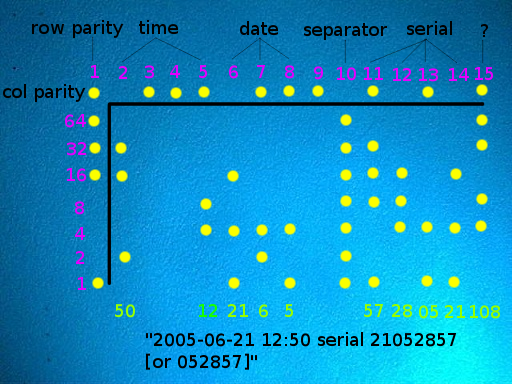
 The pattern consists of a dot-matrix spread of yellow dots, which can barely be seen with the naked eye. The dots have a diameter of a tenth of a millimeter (0.004") and a spacing of about one millimeter (0.039"). Their arrangement encodes the serial number of the device, date and time of the printing, and is repeated several times across the printing area in case of errors. For example, if the code consists of 8 × 16 dots in a square or hexagonal pattern, it spreads over a surface of about and appears on a sheet of size
The pattern consists of a dot-matrix spread of yellow dots, which can barely be seen with the naked eye. The dots have a diameter of a tenth of a millimeter (0.004") and a spacing of about one millimeter (0.039"). Their arrangement encodes the serial number of the device, date and time of the printing, and is repeated several times across the printing area in case of errors. For example, if the code consists of 8 × 16 dots in a square or hexagonal pattern, it spreads over a surface of about and appears on a sheet of size
 The Machine Identification Code can be made visible by printing or copying a page and subsequently scanning a small section with a high-resolution scanner. The yellow color channel can then be enhanced with an image processing program, to make any dots of the MIC clearly visible. Under good lighting conditions, a magnifying glass may be enough to see the pattern. Under
The Machine Identification Code can be made visible by printing or copying a page and subsequently scanning a small section with a high-resolution scanner. The yellow color channel can then be enhanced with an image processing program, to make any dots of the MIC clearly visible. Under good lighting conditions, a magnifying glass may be enough to see the pattern. Under  Using this
Using this
Printer Characterization and Signature Embedding for Security and Forensic Applications
Pei-Ju Chiang, Aravind K. Mikkilineni, Sungjoo Suh, Jan P. Allebach, George T.-C. Chiu, Edward J. Delp., Purdue University, 2006 (poster)
Laudatio der deutschen BigBrotherAwards 2004
{{inlang, de
Information by the Chaos Computer ClubInformation by the Electronic Frontier FoundationEFF list of printers, which do or don't print dots
(last updated 2017) Identity documents Printing software Privacy software Steganography Watermarking Computer-related introductions in the 1980s Money forgery Hardware restrictions
 A Machine Identification Code (MIC), also known as printer steganography, yellow dots, tracking dots or secret dots, is a
A Machine Identification Code (MIC), also known as printer steganography, yellow dots, tracking dots or secret dots, is a digital watermark
A digital watermark is a kind of marker covertly embedded in a noise-tolerant signal such as audio, video or image data. It is typically used to identify ownership of the copyright of such signal. "Watermarking" is the process of hiding digital inf ...
which certain color laser printer
Laser printing is an electrostatic digital printing process. It produces high-quality text and graphics (and moderate-quality photographs) by repeatedly passing a laser beam back and forth over a negatively-charged cylinder called a "drum" to ...
s and copier
A photocopier (also called copier or copy machine, and formerly Xerox machine, the generic trademark) is a machine that makes copies of documents and other visual images onto paper or plastic film quickly and cheaply. Most modern photocopiers ...
s leave on every printed page, allowing identification of the device which was used to print a document and giving clues to the originator. Developed by Xerox
Xerox Holdings Corporation (; also known simply as Xerox) is an American corporation that sells print and electronic document, digital document products and services in more than 160 countries. Xerox is headquartered in Norwalk, Connecticut (ha ...
and Canon
Canon or Canons may refer to:
Arts and entertainment
* Canon (fiction), the conceptual material accepted as official in a fictional universe by its fan base
* Literary canon, an accepted body of works considered as high culture
** Western ca ...
in the mid-1980s, its existence became public only in 2004. In 2018, scientists developed privacy software
Privacy software is software built to protect the privacy of its users. The software typically works in conjunction with Internet usage to control or limit the amount of information made available to third parties. The software can apply encrypt ...
to anonymize prints in order to support whistleblowers
A whistleblower (also written as whistle-blower or whistle blower) is a person, often an employee, who reveals information about activity within a private or public organization that is deemed illegal, immoral, illicit, unsafe or fraudulent. Whi ...
publishing their work.
History
In the mid-1980s Xerox pioneered an encoding mechanism for a unique number represented by tiny dots spread over the entire print area. Xerox developed the machine identification code "to assuage fears that their color copiers could be used to counterfeit bills" and received U.S. Patent No 5515451 describing the use of the yellow dots to identify the source of a copied or printed document. The public first became aware of MIC in October 2004, when it was used by Dutch authorities to track counterfeiters who had used aCanon
Canon or Canons may refer to:
Arts and entertainment
* Canon (fiction), the conceptual material accepted as official in a fictional universe by its fan base
* Literary canon, an accepted body of works considered as high culture
** Western ca ...
color laser printer. In November 2004, ''PC World
''PC World'' (stylized as PCWorld) is a global computer magazine published monthly by IDG. Since 2013, it has been an online only publication.
It offers advice on various aspects of PCs and related items, the Internet, and other personal tech ...
'' reported the machine identification code had been used for decades in some printers, allowing law enforcement to identify and track counterfeiters. The Central Bank Counterfeit Deterrence Group (CBCDG) has denied that it developed the feature.
 In 2005, the civil rights group Electronic Frontier Foundation (EFF) encouraged the public to send in sample printouts and subsequently decoded the pattern. The pattern has been demonstrated on a wide range of printers from different manufacturers and models. The EFF stated in 2015 that the documents that they previously received through the FOIA suggested that all major manufacturers of color laser printers entered a secret agreement with governments to ensure that the output of those printers is forensically traceable.
In 2007, the European Parliament was asked about the question of invasion of privacy.
In 2005, the civil rights group Electronic Frontier Foundation (EFF) encouraged the public to send in sample printouts and subsequently decoded the pattern. The pattern has been demonstrated on a wide range of printers from different manufacturers and models. The EFF stated in 2015 that the documents that they previously received through the FOIA suggested that all major manufacturers of color laser printers entered a secret agreement with governments to ensure that the output of those printers is forensically traceable.
In 2007, the European Parliament was asked about the question of invasion of privacy.
Technical aspects
 The pattern consists of a dot-matrix spread of yellow dots, which can barely be seen with the naked eye. The dots have a diameter of a tenth of a millimeter (0.004") and a spacing of about one millimeter (0.039"). Their arrangement encodes the serial number of the device, date and time of the printing, and is repeated several times across the printing area in case of errors. For example, if the code consists of 8 × 16 dots in a square or hexagonal pattern, it spreads over a surface of about and appears on a sheet of size
The pattern consists of a dot-matrix spread of yellow dots, which can barely be seen with the naked eye. The dots have a diameter of a tenth of a millimeter (0.004") and a spacing of about one millimeter (0.039"). Their arrangement encodes the serial number of the device, date and time of the printing, and is repeated several times across the printing area in case of errors. For example, if the code consists of 8 × 16 dots in a square or hexagonal pattern, it spreads over a surface of about and appears on a sheet of size A4 paper
ISO 216 is an international standard for paper sizes, used around the world except in North America and parts of Latin America. The standard defines the "A", "B" and "C" series of paper sizes, including A4, the most commonly available paper size ...
about 150 times. Thus, it can be analyzed even if only fragments or excerpts are available. Some printers arrange yellow dots in seemingly random point clouds.
According to the Chaos Computer Club
The Chaos Computer Club (CCC) is Europe's largest association of hackers with 7,700 registered members. Founded in 1981, the association is incorporated as an '' eingetragener Verein'' in Germany, with local chapters (called ''Erfa-Kreise'') i ...
in 2005, color printers leave the code in a matrix of 32 × 16 dots and thus can store 64 bytes of data (64×8).
, Xerox
Xerox Holdings Corporation (; also known simply as Xerox) is an American corporation that sells print and electronic document, digital document products and services in more than 160 countries. Xerox is headquartered in Norwalk, Connecticut (ha ...
was one of the few manufacturers to draw attention to the marked pages, stating in a product description, "The digital color printing system is equipped with an anti-counterfeit identification and banknote recognition system according to the requirements of numerous governments. Each copy shall be marked with a label which, if necessary, allows identification of the printing system with which it was created. This code is not visible under normal conditions."
In 2018, scientists at the TU Dresden
TU Dresden (for german: Technische Universität Dresden, abbreviated as TUD and often wrongly translated as "Dresden University of Technology") is a public research university, the largest institute of higher education in the city of Dresden, th ...
analyzed the patterns of 106 printer models from 18 manufacturers and found four different encoding schemes.
Visibility
 The Machine Identification Code can be made visible by printing or copying a page and subsequently scanning a small section with a high-resolution scanner. The yellow color channel can then be enhanced with an image processing program, to make any dots of the MIC clearly visible. Under good lighting conditions, a magnifying glass may be enough to see the pattern. Under
The Machine Identification Code can be made visible by printing or copying a page and subsequently scanning a small section with a high-resolution scanner. The yellow color channel can then be enhanced with an image processing program, to make any dots of the MIC clearly visible. Under good lighting conditions, a magnifying glass may be enough to see the pattern. Under UV-light
Ultraviolet (UV) is a form of electromagnetic radiation with wavelength from 10 nm (with a corresponding frequency around 30 PHz) to 400 nm (750 THz), shorter than that of visible light, but longer than X-rays. UV radiation i ...
the yellow dots are clearly recognizable.
 Using this
Using this steganographic
Steganography ( ) is the practice of representing information within another message or physical object, in such a manner that the presence of the information is not evident to human inspection. In computing/electronic contexts, a computer file, ...
process, high-quality copies of an original (e.g. a bank note
A banknote—also called a bill (North American English), paper money, or simply a note—is a type of negotiable promissory note, made by a bank or other licensed authority, payable to the bearer on demand.
Banknotes were originally issued ...
) under blue light can be made identifiable. Using this process, even shredded prints can be identified: the 2011 " Shredder Challenge" initiated by the DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Ad ...
was solved by a team called "All Your Shreds Are Belong To U.S." consisting of Otavio Good and two colleagues.Practical application
Both journalists and security experts have suggested that ''The Intercept
''The Intercept'' is an American left-wing news website founded by Glenn Greenwald, Jeremy Scahill, Laura Poitras and funded by billionaire eBay co-founder Pierre Omidyar. Its current editor is Betsy Reed. The publication initially reporte ...
'' handling of the leaks by whistleblower Reality Winner
Reality Leigh Winner (born December 4, 1991) is an American former enlisted US Air Force member and NSA translator. In 2018, she was given the longest prison sentence ever imposed for unauthorized release of government information to the media a ...
, which included publishing secret NSA documents unredacted and including the printer tracking dots, was used to identify Winner as the leaker, leading to her arrest and conviction.
Protection of privacy and circumvention
Copies or printouts of documents with confidential personal information, for example health care information, account statements, tax declaration or balance sheets, can be traced to the owner of the printer and the inception date of the documents can be revealed. This traceability is unknown to many users and inaccessible, as manufacturers do not publicize the code that produces these patterns. It is unclear which data may be unintentionally passed on with a copy or printout. In particular, there are no mentions of the technique in the support materials of most affected printers. In 2005 the Electronic Frontier Foundation (EFF) sought a decoding method and made available aPython script
Python is a high-level, general-purpose programming language. Its design philosophy emphasizes code readability with the use of significant indentation.
Python is dynamically-typed and garbage-collected. It supports multiple programming par ...
for analysis.
In 2018, scientists from TU Dresden
TU Dresden (for german: Technische Universität Dresden, abbreviated as TUD and often wrongly translated as "Dresden University of Technology") is a public research university, the largest institute of higher education in the city of Dresden, th ...
developed and published a tool to extract and analyze the steganographic codes of a given color printer and subsequently to anonymize prints from that printer. The anonymization works by printing additional yellow dots on top of the Machine Identification Code.DEDA - tracking Dots Extraction, Decoding and Anonymisation toolkit: The scientists made the software available to support whistleblower
A whistleblower (also written as whistle-blower or whistle blower) is a person, often an employee, who reveals information about activity within a private or public organization that is deemed illegal, immoral, illicit, unsafe or fraudulent. Whi ...
s in their efforts to publicize grievances.
Comparable processes
Other methods of identification are not as easily recognizable as yellow dots. For example, a modulation of laser intensity and a variation of shades of grey in texts are already feasible. , it was unknown whether manufacturers were also using these techniques.Pei-Ju Chiang, Aravind K. Mikkilineni, Sungjoo Suh, Jan P. Allebach, George T.-C. Chiu, Edward J. Delp., Purdue University, 2006 (poster)
See also
*EURion constellation
The EURion constellation (also known as Omron rings or doughnuts) is a pattern of symbols incorporated into a number of secure documents such as banknotes and ownership title certificates designs worldwide since about 1996. It is added to help ...
, a dot matrix spread over a bank note, which stops some printers and color copiers from processing
*
*
References
External links
Laudatio der deutschen BigBrotherAwards 2004
{{inlang, de
Information by the Chaos Computer Club
(last updated 2017) Identity documents Printing software Privacy software Steganography Watermarking Computer-related introductions in the 1980s Money forgery Hardware restrictions